X-Frame-Options Header
The X-Frame-Options Header is a simple yet crucial line of defense for websites, preventing them from being embedded into malicious sites or hijacked.
What Is the X-Frame-Options Header?
In simple terms, the X-Frame-Options Header is like a security guard for a building, ensuring only the right people enter. It decides who can and cannot display your website within a frame. Having this in place creates a digital boundary, making it harder for malicious websites to exploit your content.
Why Is It Important to Care about the X-Frame-Options Header?
Imagine a scenario where a suspicious website overlays a transparent frame over a trustworthy site. As you click thinking you're on the trusted website, you inadvertently interact with the concealed malicious site beneath. This deceptive act is known as clickjacking, and the X-Frame-Options Header helps prevent it.
Where is the X-Frame-Options Header Located?
The X-Frame-Options Header is located within the HTTP response headers of a website. When a browser requests a website, the server sends back an HTTP response. Within this response are several headers that guide the browser on handling the content. One of these headers is the X-Frame-Options.
How Does the X-Frame-Options Header Work? Diving into Directives
The X-Frame-Options Header employs a set of directives that dictate who can embed your webpage. These directives act as rules, guiding browsers on how to display content and who can frame it. Let's unpack the three core directives to understand their roles:
DENY:
This is the "Do Not Enter" sign for web content. Implementing this directive ensures that absolutely no site, regardless of its origin, can embed or frame your website. It's the most restrictive setting, offering maximal protection against unwanted framing.

SAMEORIGIN:
This is akin to an "Only Family Allowed" sign at a private event. By using this directive, you're permitting only your website to embed or frame its content. It restricts other external sites but allows for content embedding on pages within your site.

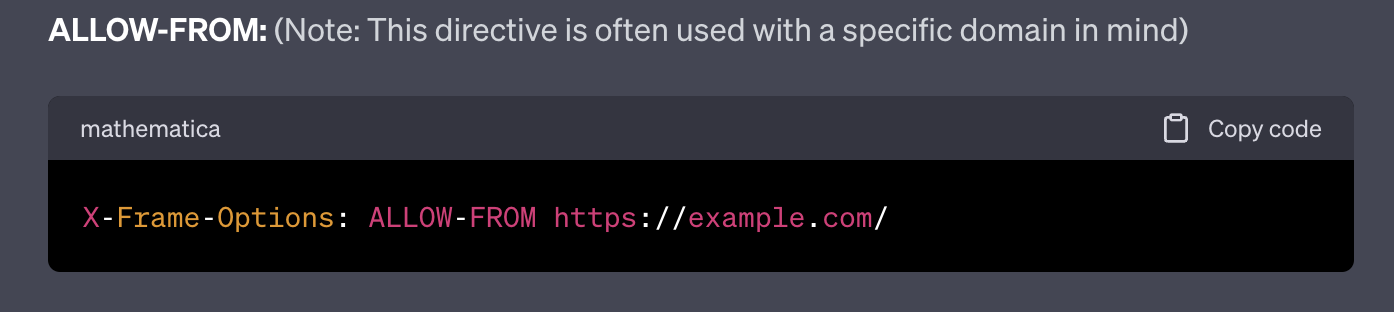
ALLOW-FROM:
Picture this as a selective guest list at an exclusive party. This directive lets you handpick specific websites that can frame your content. It's best suited for scenarios where you trust certain partners or domains to showcase your material.
Setting Up the X-Frame-Options Header: Your Implementation Blueprint
- Decide on Your Directive: Reflect on how protective you wish to be about who frames your content. Pick a directive that aligns best with your security concerns and sharing preferences.
- Integration on Your Website: This phase requires diving into your website's backend configurations. While it might sound technical, a proficient web developer or site administrator can integrate this header smoothly.
- Verification is Key: You mustn't rest easy after setting it up. It's paramount to check if your X-Frame-Options Header is up, running, and functioning as desired. Ample online tools and utilities are designed to audit and validate your header settings.
Understanding Clickjacking and X-Frame-Options Header
Clickjacking, also known as "UI redress attack," is a malicious technique where attackers trick users into clicking something different from what the user perceives. In essence, it overlays an invisible frame over a visible page. So, when users think they're clicking on one element, they unknowingly perform actions on another hidden page. The X-Frame-Options Header is designed to counteract such sneaky methods, ensuring your website isn't used as a puppet in these deceptive acts.
The Few Caveats of X-Frame-Options Header
The realm of online security is a constant game of cat and mouse. While tools like the X-Frame-Options Header offer reliable protection, it's crucial to remember that no fortress is entirely breach-proof. There may be instances where glitches inadvertently block genuine content framing. Hence, keeping a keen eye through regular monitoring and timely updates becomes a pivotal part of the defense strategy.
In Conclusion
Though the term "X-Frame-Options Header" might seem like a mouthful, its essence is pure gold for your website's safety. Envision it as the vigilant guard at your site's gate, ensuring only the suitable entities access your content. This safeguards your website and reinforces user trust, guaranteeing a genuine and seamless online experience.
FAQs
The X-Frame-Options Header is primarily used to prevent clickjacking attacks by controlling whether a browser can render a page inside an <iframe> or <frame>.
Yes, the Content Security Policy (CSP) with the frame-ancestors directive is an alternative and more modern approach to controlling which sites can embed your content.
No, the X-Frame-Options Header does not support allowing multiple domains. If you need to permit multiple domains, consider using a Content Security Policy (CSP) with the frame-ancestors directive instead.
While it's beneficial for sites containing sensitive user data or transaction capabilities, not every website requires it. However, it's a good security practice to implement it as a layer of defense against potential clickjacking.
You can inspect your website's HTTP response headers using browser developer tools or specific online tools designed to check headers. Look for the "X-Frame-Options" entry in the response headers.
